Business Scenario: Open Platform 3.0™ – Views of Environments and Processes
Business Environment
The new technologies are bringing new opportunities, such as those described under Example Business Use-Cases. But their use raises problems, which are described above under End User Pain Points. In particular, end users find that working through IT departments in the traditional way is not satisfactory. The delays are too great for rapid, innovative development. They want to use the new technologies directly – “hands on”.
Direct Purchase of IT by Business Departments
Increasingly, business departments are buying technology directly, by-passing their IT departments. Users are buying business solutions enabled by cloud services and other new technology. Traditionally, the bulk of an enterprise’s IT budget was spent by the IT department and went on maintenance. A significant proportion is now spent by the business departments, on new technology.
Convergence of Business and IT
Business and IT are not different worlds any more. Business analysts are increasingly using technical tools, and even doing application development, using exposed APIs. For example, marketing folk do search engine optimization, use business information tools, and analyze traffic on Twitter. Such operations require less IT skill than formerly because the new systems are easy to use. Also, users are becoming more IT-savvy. This is a revolution in business use of IT, comparable to the use of spreadsheets in the 1980s.
Also, business departments are hiring traditional application developers, who would once have only been found in IT departments.
Bring Your Own Device
As cellphones and tablets become more prevalent, users expect to access all resources from everywhere using own devices. These devices are being purchased outside IT department budgets, and they are outside IT department control. This raises problems for security and regulation compliance.
Dispensing with the IT Department
Some organizations have dispensed with their IT departments completely. Instead, they use integrators and cloud brokers. A corporation may use a single broker to arrange the fulfillment of its IT needs.
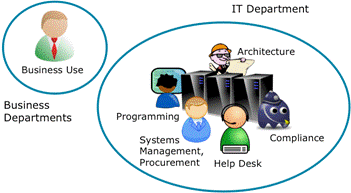
Figure 3 shows the traditional approach to enterprise IT. The IT systems are operated, supported, and managed by a specialist IT department, which may also carry out software development. Enterprise Architecture (which here typically is mainly focused on IT) and compliance are functions that are also often performed by this department.
The cloud broker IT approach is illustrated in Figure 4. In this approach, the user enterprise has no IT assets. The IT systems that it uses are operated and managed by cloud service providers. A broker assists with selection of cloud services, and provides integration and support. The broker may also carry out some development. (“Integrator” might be a better description, but “broker” is the commonly-used term.) The user enterprise consumes services provided by the broker and, by arrangement with the broker, by other IT service providers. The user enterprise is ultimately responsible for complying with regulation, and maintains a compliance capability to ensure that it does this. The user enterprise also retains control of the overall architecture, and maintains an Enterprise Architecture capability, which is now very much business-focused.
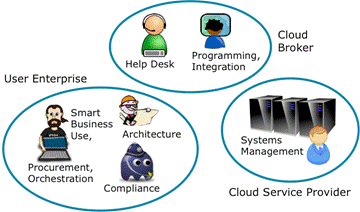
Adoption of the cloud broker approach is a particularly noticeable trend in small businesses, where everything non-core often goes outside. But some billion-dollar corporations are adopting the approach too. How far it is appropriate for a large corporation depends on the type of business that the corporation conducts. (Many of the factors affecting this decision are described in the chapter on Establishing your Cloud Vision in Cloud Computing for Business [CCBusiness].)
Retaining control of the architecture makes the user enterprise less dependent on the broker. Agreed risk and performance models enable the user enterprise to monitor service provision and resolve issues.
Spectrum of Approaches to IT
The cloud broker approach is, however, just one point on a spectrum of approaches to IT that range from having IT completely in-house to full outsourcing in which some business processes, as well as IT, are moved to external organizations.
Many organizations will adopt a hybrid approach, with some applications managed by the IT department and others by one or more brokers.
Also, IT departments will increasingly act as internal brokers of their own private clouds and external cloud services, as illustrated in Figure 5.
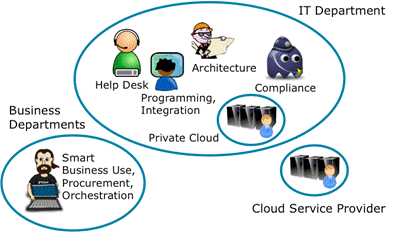
This approach will be particularly effective where enterprises need to keep IT services in-house for security or regulatory compliance reasons, but want to use new technology “hands on”.
Business Drivers
Traditional business drivers still apply, but enterprises are now also looking to gain advantage from innovation based on use of new technologies. They still want to grow revenue, increase operating margin, increase asset efficiency, and increase management efficiency. They also want to find new business models, identify new products and services, and improve delivery of existing products and services, using the new technological possibilities that are available to them.
Example Business Use-Cases
The new technologies are enabling new business processes, leading to exciting new business opportunities. Here are some of the actual and potential use-cases that have been identified by the Open Platform 3.0 Forum. The descriptions here are derived from, but not identical to, the use-case descriptions produced by the Forum’s Business Use-Cases activity, which are intended for separate publication.
Retail Smart Store
Using sensors, a retail store tracks the behavior of customers browsing the goods on display, and provides them with information and advice via their mobile devices.
Sustainable Shopping and Restaurant Street
Sensors and controls are used to minimize energy usage in a city street. (An experiment including this has been launched in Amsterdam [ASC].)
Augmented Patient Care Sensor Feedback
Sensors monitor hospital patients and information and alerts are given to healthcare professionals on their mobile devices.
Incident Management
Incidents such as natural disasters, terrorist attacks, etc. are reported into social media by responsible citizens. Weather channels may report weather-related disasters as well. Systems analyze the data coming from these sources, validate the data, analyze the truth of data based on information collected from multiple sources, and report the incidents to relevant parties such as protective services, health services, and voluntary organizations. These parties take steps such as helping with evacuations, transport, healthcare, and supplies (food, shelter, clothing) for the people affected.
Translational Research – Bench to Bedside
Clinical researchers conduct disease research, which is referred to as bench-side, while treating the patients at the bedside. This involves processing large amounts of data, which are collected, analyzed, and stored for each patient. The researchers combine the data from multiple patients and derive patterns of interest. Over time this leads to algorithms that enable clinicians to identify conditions quickly for effective treatment.
Social Media Marketing
Companies obtain information on existing and new consumers who use social media from the social media networks. They use big data analytics to identify trends. They conduct marketing campaigns through communication to the social networks, and can target messaging to specific consumer group profiles.
On-Demand Development
A distributed development platform blends a global talent marketplace with collaboration tools and cloud infrastructure, enabling businesses to hire developers on-demand and have them work on cloud-based infrastructure (preconfigured remote desktops and servers to be used for development and testing). The platform helps businesses get technology solutions developed at a substantially lower cost than traditional outsourcing models without compromising on quality or security.
Electric Vehicles Ecosystem
An open web-based system enables companies and people concerned with the development, production, and operation of electric vehicles to share information. Much of this information is obtained from sensors on the vehicles and associated equipment. Designers and manufacturers can then monitor vehicle components and their behavior, and improve their design. Maintenance management services can anticipate failures through battery lifetime monitoring, incident detection, and cloud storage of users’ information. User management services can direct vehicles with drained batteries towards a nearest charging station taking into account the other vehicles’ batteries within a given perimeter. Drivers can have dashboards showing information such as engine and wheel status, battery status, recommended maintenance date, identification of the nearest geographic location of electrical vehicle plug-ins, current location analysis, and itinerary recommendations.
Safe Mobility
This concept applies to children travelling from home to school, but it is also extendable to elderly people or patients, and women travelling alone at night. When a child leaves home, it wears an article of clothing with an embedded RFID tag. The event is read and recorded by the intelligent home infrastructure, and may be forwarded to the parents as a text message, email, or similar, if required, or only if the event deviates from the scheduled or “learned” expected behavior. Intelligent homes in the neighborhood, the bus stops, and the road infrastructure share the required information on the number of children and their destination, enabling the optimal routes to be scheduled. Different means of transportation may be customized according to the actual needs, such as pedibus, multi-modal, or “parent taxi”, and given priority access. Non-essential or through traffic is diverted away from the school area. On arrival at the school, specific vehicle access is granted by sending a 2D code, a near field communication certificate, or some similar means of identification to the driver’s smart-phone. The children who were identified when entering the vehicle are checked when entering the school. The reverse procedure is operated when the children go home.
Technical Environment
Characteristics and Trends
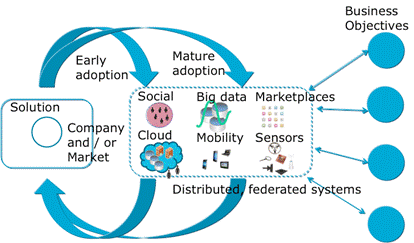
Today’s technical environment is characterized by the emergence of a number of phenomena that disrupt traditional IT models. These phenomena include social computing, mobile computing, cloud computing, big data, and the Internet of things (sensors and controls). Given the current pace of technological development, we may see further disruptive phenomena emerge in the near future. Cognitive computing, for example, appears a likely addition to the list.
These technologies may be used singly, but can be especially powerful in combination. For example, big data analytics can be used in combination with social media to identify social trends and develop market forecasts.
The developing technology landscape as seen by one major industry player is described in the IBM Global Technology Outlook 2013, which identifies the following major trends [IBM2013]:
- Mobile First
- Scalable Services Ecosystems
- Software-defined Environments
- Multimedia and Visual Analytics
- Contextual Enterprise
- Personalized Education
These trends are related to the new technologies. For example, mobile first is directly enabled by mobile computing, and scalable services by cloud computing. In other cases, the relationship is less direct. For example, scalable services ecosystems and contextual enterprise are new business patterns made possible by the technology.
Specific Technologies
Social Computing
Social computing refers here to computing related to or using social media. Social media are a development of Internet and web technology. They provide a means of interaction among people in which they create, share, and exchange information and ideas in virtual communities and networks [Ahlquist].

Some Social Media in Common Use Today
They can help businesses to communicate, to understand people, and to forecast trends. This is valuable for purposes such as marketing, sales, partnering, recruiting, and internal communications.
Mobile Computing
Mobile computing is achieved through the connection of portable computing devices to servers via mobile radio networks and the Internet. It is based on the convergence of computing and mobile telephone technology.

Some Mobile Computing Devices in Common Use Today
It enables people to access IT anywhere, and on the move. It unchains people from their desks, and helps them to work better, faster, and cheaper.
Cloud Computing
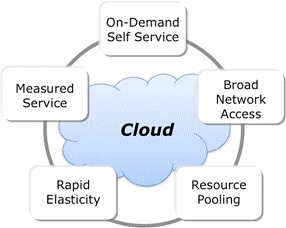
The essential concept of cloud computing is that IT resources are made available, within an environment that enables them to be used, via a communications network, as a service. A cloud service has the five essential characteristics of on-demand self service, broad network access, resource pooling, rapid elasticity, and measured service.
Cloud computing enables business to focus on its core capabilities, and operate better, faster, and cheaper.
Big Data
Big data refers to data that is so large that it is difficult to work with using IT systems available today. There is a growing body of analysis, visualization, and distributed processing software that enables people to extract useful information from such data. Often, the people extracting the information do not know what they are looking for, so that the algorithms are modified and refined as the search proceeds and as potentially interesting aspects of the data come to light.
Big data analytics enable users to obtain a better understanding of their environment, and hence to take better decisions.
The Internet of Things
The Internet of things refers to uniquely identifiable objects and their virtual representations in an Internet-like structure. It is generally used to mean the connection of sensors and controls to the Internet, so that enterprises can monitor the activities and operation of people, machines, buildings, engineering structures, and the natural environment, and, in some cases, control that operation.

A Few Sensors in Common Use Today
Given the vast number of things in the world, and the ability of sensors to generate data automatically and continuously, the Internet of things is forecast to lead to an explosion in the amount of data available for processing.