|

Service Oriented Infrastructure (SOI) involves the application of
fundamental principles of service orientation to the underlying infrastructure
that enables all applications - service oriented or otherwise - to effectively
and efficiently operate to deliver business value to the end users.
As such, a service oriented infrastructure can be regarded as a natural part of a
service-oriented enterprise architecture involving the definition and
provisioning of IT infrastructure in terms of services.
The architecture encompasses all phases of the service life cycle, including the design,
provisioning, operation, decommissioning, and management of the services. It is
relevant to the mapping to
business processes of underlying infrastructure and IT assets.
Infrastructure architecture is regarded by many as one of the
three pillars of information technology, together with business architecture
and application architecture.
Service-oriented infrastructure results from
applying the principles of service-orientation to this architectural pillar.
It is related to service-oriented architecture (SOA) which is most commonly
used to refer to the use of this principle in application architecture.
 Differentiating characteristics Differentiating characteristics
In contrast to other infrastructure architectures, a
service-oriented infrastructure has the following differentiating
characteristics.
- The infrastructure is defined as a set of technology-agnostic,
standardized services.
- The applications are decoupled from the infrastructure.
- The infrastructure services are delivered from a pool of resources
governed by a centralized management system that balances supply and demand.
 SOI Reference Model SOI Reference Model
The figure below shows the SOI Reference Model.
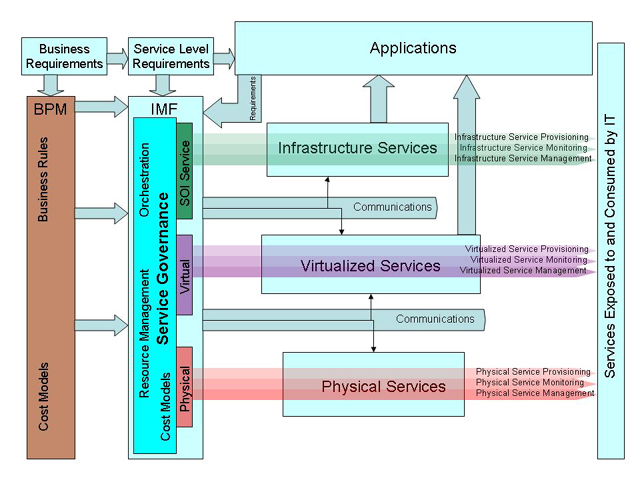
The elements of the reference model are described below.
 Business Requirements Business Requirements
In the SOI context, business requirements
are generated from both the business of the enterprise and the business of IT.
The enterprise business requirements are captured in internal service level
agreements (SLAs) as well as other factors not always specified in the SLAs such as
cost models.
The business-of-IT requirements are tied to the capability of the
organization, cost metrics, vendor relationships, and strategic direction of
the IT organization.
These combined requirements drive the
activities of the BPM (Business Process Monitoring) and Service-Level
Requirements building blocks of the reference model.
 Service-Level Requirements Service-Level Requirements
The service-level requirements define the
levels of service to be delivered and the remedies when they are not. This
includes the services delivered by the infrastructure to other services,
services delivered to IT personnel, consuming services, and higher level infrastructure
services consumed by business users and applications.
 BPM BPM
Business process monitoring is the set of
rules, cost models, and other factors that are derived from the business
requirements of the enterprise and business of IT. This in turn is one of the
key drivers for the IMF (Infrastructure Management Framework).
 IMF IMF
The infrastructure management framework is
the collection of software, processes and procedures
that are used to plan, build, and run the IT
resources and services in accordance with the business and service level
requirements.
 Applications Applications
These are software programs that support business functions.
In a service-oriented application architecture,
they include programs that perform the portfolio services
described in the
section on The Building Blocks of SOA.
 Services Exposed to and Consumed by IT Services Exposed to and Consumed by IT
These are services that the IT organization uses to plan,
build, and run the enterprise to deliver on the IT needs of the business.
 Infrastructure Services Infrastructure Services
These are the services that expose the infrastructure capabilities.
An infrastructure service may be composed of other infrastructure services,
virtualized services, and physical services.
Infrastructure services typically use and/or provide a
virtualized pool of shared resources (servers, network, storage, infrastructure
software) which are deployed and managed in an automated fashion.
The foundational principles of composition of services apply to
infrastructure services just as they do within the application domain.
Infrastructure services exposed to the business and applications world
can be any one of the pure-play, cross-application and operational services.
These services are consumed to varying degrees during the different phases of
the software application lifecyle.
- Pure-play infrastructure services are specific to the
provisioning of infrastructure components like servers, storage, content etc.
that are consumed throughout the development, deployment and management of
applications.
- Cross-application infrastructure services are not specific to the business functionality within any given application, and apply across multiple applications. These services are consumed more often in the production environment.
- Operational infrastructure Services facilitate the creation
of the environment required to enable the delivery, deployment and management
of applications over multiple phases of the software development lifecycle.
Each of these types of service can be composed of
infrastructure services of the other two types.
Pure-Play Infrastructure Services
Pure-play infrastructure services are rooted in the elements specific to
hardware, network, storage, data, and other similar non-software elements.
The term Infrastructure-as-a-service refers to the
provisioning of a combination of these elements in a technology-agnostic fashion.
Virtualization is one of the key technological and architectural
concepts that are employed by pure-play services.
Some examples of such services include:
- Storage Services - storage and retrieval of any amount
of information at any point of time from anywhere.
The information that is shared is more important than its underlying location
and storage structures.
These services ensure that the specific technological details about the nature
of the storage media used, the data access and manipulation mechanisms are not
exposed to the consumer.
- Content Delivery Services - delivery of content to the end-user
on a varied set of end-user devices.
Here again, the underlying technology of
the devices employed by the consumer and/or the content transmission
infrastructure are hidden from the end-user.
Content may be assimilated from multiple locations
and delivered to the consumer as an integral unit of information.
- Database Services - composite database services.
The interface to the service needs to follow standards, e.g. ODBC.
This provides an open interface, hiding the actual details of the service from
its consumers. The ODBC service can rely on various building blocks. A possible
stack is shown below.

- Compute Services - using the idle CPU time within a network of servers
to execute tasks.
The foundation for such services was provided by the grid computing initiative,
which is re-surfacing today as infrastructure services that can be employed by computation-intensive applications.
Cross-Application Infrastructure Services
Such services are not specific to the functional capabilities of
an application.
Instead, these are common services that apply across all
applications regardless of the business functionality or industry they operate in.
Examples of such services include:
- Queuing Service - assures guaranteed delivery of messages between applications.
This queuing service can have built-in location transparency
that enables the more effective execution of the inter-application communication
across data centers and geographies.
- Authentication service - authentication of the credentials
provided by end-users to gain access to applications.
This involves a common, well-defined combination of steps.
The level of authentication may vary depending on the nature of the application
and the business-related security requirements.
Multiple authentication models can be made available by these services.
Operational Infrastructure Services
These services enable the standardization of the manner in which
enterprises build, deploy and manage solutions for themselves and their customers.
These are not specific to the business process or the application functionality.
Instead, these are services that enable the foundational
aspects of constructing, validating and implementing a software solution.
Examples of such services include:
- Configuration Management Service - tracks changes to
the configuration of applications and infrastructure.
This service should accommodate all types of configuration item,
and the business rules that govern their modifications across all architectural layers.
- Continuous Building Service - enables the continuing construction
of the software components required to be incrementally tested and deployed on a regular basis.
The nature of this service is such that it is not specific to the software solution being constructed or the frequency and complexity of the inherent dependencies within a build.
- Remote Management Service - enables the remote management
of processors so that appropriate corrective action can be taken in the event of an impending failure being detected.
These services enable the expeditious execution of these corrective actions without any requirement for physical presence near the servers.
 Physical Services Physical Services
The physical services are the atomic level
of this model and represent the hardware, operating system, and personality
(role based configuration) of computing, storage, and transport technologies.
 Virtualized services Virtualized services
Virtualized services expose the capabilities of physical devices
in a device-independent way.
A model for virtualization is described in the
section on Detailed Models for SOA Features.
Some examples of virtualized services are given below.
- Database virtualization
Database virtualization allows users to access various sources of
disparately located data without knowing or caring where the data actually
resides. Database virtualization allows the use of multiple instances of a
DBMS, or different DBMS platforms, simultaneously and in a transparent fashion,
regardless of their physical location. These practices are often employed in
data mining and data warehousing systems.
- Middleware virtualization
In the server-centric world, middleware is used to provide common
infrastructure services, such as application containers, data and messaging. To
ensure that the same model works in a cloud environment (i.e., a computing
paradigm shift in which computing is moved away from personal computers or an
individual application server to a "cloud" of computers), all those
components must be virtualized. That is to say virtualization of the container,
the data, and messaging. In so doing, the application is abstracted from the
fact that it is running on a "cloud" and enables the transition from
a server-centric model to a cloud computing model. Middleware virtualization
breaks down the common infrastructure services (application containers,
messaging, and data) and de-couples the APIs from the runtime platforms used to
serve the API. The underlying runtime system provides common services for
availability, and supports other characteristics of the service as defined in
the contracts for the service (e.g., scalability, integrity of the data,
service window, etc.).
- Server or Host Virtualization
Server or host virtualization handles the process of abstracting
logical compute resources from physical compute resources.
Operating system virtualizations encapsulates the
entire operating system from the hardware.
- Network Virtualization
In a virtualized network, multiple virtual networks co-exist on
top of a shared substrate of multiple physical networks.
Different virtual networks provide alternate end-to-end packet delivery systems
and may use different protocols and packet formats. Virtual networks are
implemented by virtual routers connected by virtual links.
- Storage Virtualization
Storage virtualization refers to the process of abstracting
logical storage from physical storage. The term is used to describe this
abstraction at any layer in the storage software and hardware stack.
Storage virtualization typically hides the complexity of the back-end processes and
devices from the users or servers that access the storage.
Basic storage virtualization could combine two physical storage disks and make them appear as
a single logical disk drive.
|
