

Securing Your Business
A White Paper
Dean Adams
Director, Security & Electronic Commerce
The Open Group
For open system suppliers and buyers worldwide, the economic imperative today is to increase productivity and reduce costs. The Open Group defines the necessary products, services and processes to achieve these and other business objectives.
The Open Group leads collaboration among customers, systems and software vendors, other consortia and standards groups, to consolidate, prioritize and enable timely vendor responses to customers current and future requirements by:
organizations world-wide have increasingly come to depend upon open systems-based computing systems to help manage their operations and to transact business with trading partners. With this dependence comes a growing concern over security.
Solutions for dealing with security issues have been fragmented and inconsistent, resulting in higher costs to both end-user organizations and to hardware and software vendors. Lengthy and expensive evaluations, a plethora of incompatible security products and the lack of clearly defined standards have led to wasted duplication of effort and have slowed the globalization of electronic trade.
This document discusses the security challenges posed by standalone, distributed and public network-based computing environments and the opportunities offered to end-users and vendors by the evolving standards-based solutions developed by The Open Group.
Customers are a vital force in the development of these new solutions. Together with the leading systems and software suppliers, over 150 of the world's largest enterprises form an effective working partnership to ensure that the right combination of features are provided, and that both standard specifications and technology are fit for purpose.
Businesses have invested heavily in open systems computing and networks over the past decade. This trend is certain to continue as the world becomes increasingly competitive and organizations are compelled to reduce costs and increase value-added services to their customers.
Companies and public sector organizations alike have come to depend on computer-based information systems, and with that dependence has come growing awareness and concern for security.
Much of the attention has been focused on deliberate abuse by unauthorized users committing equipment theft, data falsification, system or data sabotage and the deliberate misuse of corporate computers. External threats, though a real problem, are generally responsible for fewer losses than those that are internal to the organization. Most security-related incidents and subsequent losses have been due to accidents or errors, not hostile attacks. Software and hardware can malfunction. Programming and end-user errors can occur. In the distributed computing world, such problems arise because these environments tend to be more complex and, subsequently, harder to manage.
Seeking to protect themselves and their computing systems, organizations have turned to hardware and software vendors for solutions. Vendors have responded with a seemingly endless variety of security products.
At first glance, the security product industry appears to offer businesses an ample selection of security solutions. Upon closer examination, however, we see that organizations are presented with many solutions with little in common. These products are as diverse as they are numerous. In the absence of standards, each vendor's products are proprietary, created independently with no regard for inter-vendor compatibility.
The resulting diversity of products leaves end-users confused and overwhelmed with alternatives, offering no mechanism for consistent evaluation or selection. This diversity not only increases the cost of evaluation for organizations, but also adds to the cost of implementing and maintaining systems securely.
In today's computing world, it is costly to bring products to market. Vendors must undertake testing and certification of new products, which can run to tens of millions of dollars. Undergoing formal evaluations can also delay product introduction into the marketplace, adding as much as three years to the process. Extended evaluations tend to slow new product evolution. Revenues from new products similarly tend to be delayed, further costing vendors money.
The cost of providing security can be expensive for end-user organizations as well. Many organizations use a variety of systems to conduct business. Multiple platforms, supplied by different vendors, complicates the process of supporting security policies and leads to uneven security support. organizations must rely on expensive staff to evaluate and compensate for differences among systems to level the playing field. Early adoption of useful technology can be delayed by vendor certification processes. End-users seeking leading-edge products must either wait for evaluations to be completed or make their own evaluation as to suitability within their computing environment.
While ensuring system security can be expensive, it can also be cost effective. In fact, the traditional image of security as an insurance policy is no longer accurate. Standard security can, in fact, be considered a cost-reduction tool cutting administrative and maintenance costs through the provision of consistent facilities across all systems and through the reduction of costly errors.
With standard security features in place, end-users can reduce the need for costly custom countermeasures. Errors can be expensive. Preventing them reduces the overall risk and cost of ownership over the life of the system.
Vendors, too, benefit from offering secure open systems. With potential customers' concerns over security put at ease, open systems vendors can more effectively compete with proprietary alternatives by offering competitive pricing, which can lead to increased sales.
Fewer and fewer computers operate without communication and interaction with other computers. The standalone computer has given way to complex, enterprise-wide networks and distributed computing environments. With the migration to distributed networks, security becomes a larger, more pressing issue. While the need to address security issues at the enterprise-wide level is evident, the first logical step toward building a secure computing environment begins at the system level.
A structurally solid building requires a solid foundation. Similarly, a consistent base of individually secure platforms is required upon which to build secure enterprise-wide computing environments. Defining security at the system level represents the first step toward a secure enterprise-wide environment.
There are also significant cost-of-ownership savings to be made at the system level. Multiple systems with different security parameters are more costly to manage. Defining a single set of security parameters across all systems reduces duplication of effort and costs and simplifies installation and ongoing maintenance.
But the best reason for beginning at the system level is that it can be done now. Specifications are already well defined, and support by a critical-mass of end-users and vendors is assured.
Before solving the security concerns of distributed computing environments, a number of issues must be dealt with at the system level. In addition to addressing associated vendor-specific functionality and settings problems, systems should be provided with a set of functionalities oriented towards commercial business, not military or classified government use. Ensuring the elimination of significant flaws in the majority of current systems, such as the over-dependence upon super-user in the UNIX® operating system, must also be dealt with.
Hardware and software vendors have long recognized the need for secure open systems. Each has independently evolved functionality and settings for security specific to their products. With identical functionality and settings, organizations that operate homogeneous computing environments have minimal difficulty installing and maintaining systems securely throughout their networks.
Many businesses are, themselves distributed, spread over several sites, incorporating various autonomous business units. Each unit may make purchasing decisions based on individual business requirements as well as local product availability and support levels. Unlike organizations with homogeneous computing environments, these enterprises must cope with varying functionality and settings when attempting to support a corporate security policy.
In spite of diligent attention to security by system administrators, most open systems provide for a category of user known as super-user. This super-user enjoys the highest level of authorization and can bypass most security checks on the system. The super-user, obviously, provides an opportunity for security abuses from both internal and external users. Super-users can also, by the nature of their powers, circumvent many protective measures, including auditing.
The solutions to the above system-level security concerns are obvious. First, define a common set of functionalities and common default settings that would level the playing field and provide consistent functionality and settings across all platforms, regardless of vendor or product. Second, provide facilities to define and limit the functional roles of users.
A good standard, one that had the best interests of customers in mind, would specify vendor defaults for the correct level of security when products were installed. This would ensure that systems were installed in a secure way before users have access to them. And all systems, regardless of vendor, would conform to the same settings.
If that standard also provided the ability to define functional roles, it would reduce the potential for individuals performing the wrong tasks or actions. For example, one individual might be responsible for system back-up while another was responsible for restore. Though both roles require access to the same resources and data that resides on disk drives and archiving devices, the roles are defined that allow individuals to perform specific operations, but not others.
Such a standard has been created. The Open Group has defined a product standard for Baseline Security Services. Baseline Security 96 is a platform-neutral product standard that defines a basic, standard set of security facilities that should be made available on a computing platform. In addition, it defines reasonable and safe default security parameters that are mandated on delivery of the system.
The Baseline Security 96 is based on the X/Open Baseline Security Services specification (XBSS). This specification was achieved through a long-term series of negotiations and sessions involving all major vendors and end-users from over 150 of the world's leading industries. Computers that conform to XBSS specification provide users with a level of confidence that systems will work safely and securely and are compatible with other such systems, regardless of the vendor.
The XBSS defines seven areas of functionality:
Baseline Security 96 will be improved upon with subsequent enhancements. Additional phases will address successively more complex issues, such as fully distributed application environments.
While some systems operate in a standalone environment, enterprise-wide networking is where most of the computing world is, or is headed, today. Systems are communicating with other systems (an interconnected environment) and, increasingly, applications are being distributed among systems (a distributed computing environment). Such complexity presents a number of significant threats to security.
Distributed systems share many of the same security concerns found in standalone environments. But, because of their more complex structure, these concerns are multiplied. Those of particular concern involve auditing, system back-up and restore, secure communication and management of password accounts.
In a distributed environment, systems and the various software components of business applications are spread across the network. The ability to audit distributed business applications as a single entity within the distributed environment is vital. This is particularly true in the event of an attack. Such an attack could involve one system or many. With a distributed auditing facility in place, important clues to the location, nature and timing of the events of the attack could be quickly identified, which might otherwise be missed if analized system by system.
While financial auditing practices are typically consistent throughout a large company, the same cannot be said of computing system environment auditing practices. Auditing records and procedures may vary from system to system and from location to location. Such inconsistencies make centralized auditing virtually impossible, resulting in duplication of effort and added management cost.
Systems can, and do, go down. Information can, and will, be mistakenly deleted or modified. With uniform procedures in place for back-up and restore of systems, end-users have little to worry about beyond the loss of computing time. Without uniform procedures in place, opportunities for errors such as incomplete back-ups or unauthorized or inexperienced personnel performing system restore (with occasional catastrophic consequences) can occur.
In enterprise-wide environments, businesses require facilities that enable the back-up and restore of large segments of environments, rather than individual systems. Such environments also require effective protection of networked back-up and restore resources and the protection of information being archived from across the network.
Without communications, distributed computing cannot function. Ensuring that communications between all entities-both applications and system resources-in a distributed environment are secure is essential. Secure communications services must be provided in a standard manner on all systems if business applications are to take advantage of those communications on all platforms without the need to be redesigned. If security mechanisms on various systems are incompatible, the task of securing communications becomes exceedingly more difficult.
Frequently, users must access multiple systems within a distributed network in the normal performance of their jobs. This usually requires separate accounts and passwords for each system that must be accessed. End-users may find it difficult remembering or managing multiple passwords, often relying on the insecure practice of posting passwords on the sides of desks or terminals. With job changes occurring regularly, employees leaving and new employees being hired, system managers can find account and password management taking up a significant proportion of their time and, consequently, a notable proportion of the corporate IT budget.
The information technology industry has been well aware of these concerns and has put a great deal of time and effort into solutions. A substantial document, the X/Open Distributed Security Framework (XDSF), was published in 1994. This document defines a framework for securing distributed systems.
The XDSF is a blueprint for the development and implementation of security services in a heterogeneous distributed environment. This document provides a foundation for migrating from platform-focused to distributed open systems by defining generic security application programming interfaces (APIs) that are independent of specific underlying security mechanisms. It does not contain specific conformance recommendations, like the XBSS. Rather, it lays the ground work for The Open Group product standards to come. The figure below illustrates an application programmer's view of the X/Open Distributed Security Framework as a block diagram.
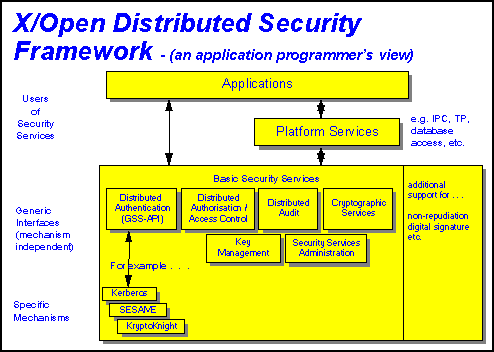
The security services listed in the diagram are not intended to provide an exhaustive list of those covered by the Distributed Security Framework. These are only examples, and serve to illustrate how security services are to be provided, wherever possible, in a generic form, insulating the application or platform service from the specific security technology being used. Business applications wishing to secure their operations may take advantage of secure versions of platform services, such as database access services or inter-process communications; e.g., Remote Procedural Call (RPC) or sockets. These platform services can secure themselves through use of the security services. When secure versions of platform services don't exist, or the business application has special needs, business applications can directly use the security services themselves to ensure secure operation.
Since completing this framework in 1994, The Open Group has concentrated on delivering detailed specifications for the services that it describes. Of particular note, in the context of enterprise-wide environments, are the Secure Communications Services, Distributed Audit, Generic Cryptographic Services, Secure Backup and Restore, and Single Sign-On.
Under Distributed Authentication, and recently released as a separate specifications document, the Secure Communications Services (based on GSS-API), enables software entities within a distributed environment to mutually authenticate to one-another, and provide ongoing protection of the communications between them.
The Distributed Auditing Services specification defines a mechanism for enabling a centralized archiving and analysis of audit trails in a distributed heterogeneous environment.
A useful by-product of the Distributed Auditing Services specification is audit trail portability. The specified format can be transported from system to system, simplifying management and analysis, even in an interconnected, non-distributed application computing environment.
Secure Back-up and Restore is a critical operation for large commercial users. Work is currently underway by The Open Group on a product standard that addresses end-users' concerns for confidentiality and integrity of information when systems are either backed-up or restored in a distributed environment.
One of the most hotly discussed topics in IT today is cryptography. Currently, there is no accepted international standard for an encryption technology that can be used around the world. Countries have varying laws regarding the export of encryption technology, and some even forbid its use. This situation has hampered the development of secure, portable business applications that can take advantage of cryptography and has increased costs to vendors who must provide different and independent implementations of cryptographic facilities in different parts of the world.
In response to these problems, The Open Group has defined a Generic Cryptographic Services specification. This specification provides isolation from the underlying technology and also the nature of the implementation, whether hardware or software or some combination of the two. The application is free to assume as little, or as much, responsibility for the control of the underlying cryptography as it wishes.
If strong, effective security services and applications are required, users must eventually come to rely on cryptographic tools to provide protection. Encryption, for example, offers the best means to secure audit trails and communications. Cryptography can also provide integrity protection, enabling end-users to detect tampering. Cryptography will be required for the support of many other security services and applications.
A future specification, Single Sign-On will ease the burden of system managers who must control access to distributed systems, and to end-users who must currently remember multiple passwords when accessing multiple systems. The specification will give end-users the ability to sign on to the "corporation," as a whole, rather than requiring sign-on to each individual computer that they need to access.
There is currently a tremendous interest within the commercial marketplace to be able to take advantage of a public network, like the Internet, to increase the level of business with existing customers, to find new customers, and to conduct business at lower cost.
Already, many organizations are using the World Wide Web as an additional channel through which they can advertise their products and services. Information and software updates are being cost-effectively provided to customers via the Internet, and many companies are running Internet services within their own corporate networks (Intranets) to improve information flow and access with a view to improving their performance, teamwork and customer-responsiveness.
The Internet currently provides little, if any security. User names and passwords are effectively transmitted in the clear when using typical Internet services, such as the telnet services for remote terminals or the ftp file transfer services. Communications via email, in most cases, are not sufficiently protected from tampering or exposure to unknown parties. Identities can be forged resulting in communication with someone other than the person that you thought you were communicating with.
To use the Internet to conduct real business; i. e., exchange contracts, buy and sell goods and services, issue delivery notes, receipts, invoices, etc.; an entirely new set of facilities must be made available, such as confidentiality and integrity protection, digital signatures and non-repudiation services, among others.
If the Internet is to provide a new, alternative method of doing business to the existing practice of using paper, it must be capable of providing irrefutable evidence, or proof, that a particular transaction has occurred. It must also be capable of irrefutably proving that particular entities were involved in a transaction, and must be able to counter any claims by any party that, for instance, documents were neither sent, nor received by them at a particular time.
Irrefutable evidence can be essential to support a re-negotiation or a court case in the event of unplanned delays, hidden expenses, mistakes or wrongdoing. If this evidence or proof cannot be provided irrefutably to the satisfaction of a court of law, then electronic trading practices cannot be counted on to meet the needs of business.
Connecting to the Internet involves risks for most companies. Hackers are, regrettably, a fact of life and industrial espionage is on the rise. A company that wishes to use the Internet solely for advertising purposes, for instance, must isolate its corporate network, which carries all its valuable information assets, from the public Internet.
Many companies will seek to make extensive use of the Internet, going well beyond isolated applications such as advertising, conducting various levels of business between diverse company locations and with trading partners scattered around the world. The leading solution to the problem of securing these Internet-based communications is the firewall.
An effective firewall reduces risks by ensuring a limited number of well-managed choke points for corporate connections with the Internet. These choke points provide a filter, or guard, that keeps potential harmful intruders or programs at bay. They also prevent leakage, or eavesdropping, of corporate information onto the Internet.
There are many firewall products available on the market today. The number of products and competing claims present a confusing situation for end-users. Large enterprises with autonomous business units often buy different products, resulting in incompatibilities among firewall products and, ultimately, increased management costs.
Work is presently underway to provide an Internet Firewall product standard. This product standard will ensure that customers can obtain firewalls that exhibit features deemed necessary by a wide-ranging industrial college of experts, and which are compatible with other products that conform to the standard. This standard will also provide associated facilities to allow for Virtual Private Networking (VPN).
VPN enables an enterprise to replace its expensive leased lines, used for communications between corporate sites, with Internet connections. As information passes out of a corporate site, it is automatically encrypted and transmitted over the public Internet to the receiving corporate site. As it enters the receiving site, the information is decrypted again. In addition to providing corporate communications at a lower cost and higher flexibility than leased lines, this type of communications will support improved redundancy and reliability, since the Internet can provide multiple paths to a destination.
Cryptography is necessary to support secure communications and is an important supporting technology for electronic commerce. For electronic commerce, however, providing irrefutable evidence of, for example, transactions or authenticity, will be the deciding factor in its success. Cryptography is not only of interest to business, but also to governments-many of whom are restricting the export of cryptographic technology. In some cases, even the use of encryption is forbidden. Governments are legitimately concerned that criminal organizations may carry on their activities undetected by law enforcement agencies. These issues must be resolved if business is to take advantage of the opportunities inherent in electronic commerce.
Work is underway to resolve these issues and to define standards for practical solutions for the commercial marketplace. For example, it may be possible to define an electronic warrant that would enable law enforcement agencies, subject to due process of law, to obtain access to encrypted information where wrongdoing is suspected.
The Open Group favors the business use of strong cryptography to protect assets and communications. If provision is not made for law enforcement to continue in a practical manner, the restrictions on the export and use of cryptography may continue. The Open Group is working with others to examine mechanisms that allow for law enforcement agency access, subject to due legal process, without otherwise compromising corporate or private security.
Public key cryptography can provide the underpinning for various vital services that are required to support electronic commerce and which are scaleable on a world-wide basis. The idea behind public key cryptography is simple. Anyone can encrypt a message, but only the receiver can decode it. Two keys are created: private and public. They are created as a pair by a complex mathematical algorithm. The sender must encrypt a message with the public key of the receiver. The receiver decodes the encrypted message with the private key. Only the receiver knows the private key, which is unique to that individual and, thus, is the only one who can access the message.
Public key cryptography can provide other services in addition to confidentiality, such as integrity protection, wherein tampering of information can be detected, and digital signatures, which can support the authentication of information and its source and which can also ensure accountability for actions. Finally, non-repudiation services can be provided that can counter claims by any party that documents or messages were neither sent nor received by them at a particular time.
Business today is conducted between arbitrary parties on a world-wide scale. In the same way that telephone numbers of suppliers of products and services can be looked up in a directory, in an Internet-based electronic commerce environment, organizations will need to get hold of public keys belonging to arbitrary entities, such as people, companies, or the machine representatives of people or companies. This will necessitate world-wide directory service from which companies can request keys. Requests for a particular key will not be a one-time event, as keys can be exposed, simply lost, or will have to be changed regularly according to individual company policy. The entire life cycle of keys will have to be managed from creation, through distribution and usage, retirement and archival, to their eventual destruction.
The Open Group is working on key management and in conjunction with experts from the Internet Engineering Task Force and other organizations, is developing a common architecture for a Public Key Infrastructure. This makes use of detailed specification work being done in both organizations on protocols, programming interfaces and data formats. It is intended to fit with existing practice and does not for example, expect to mandate any particular directory service for the location or storage of keys and certificates, but will accommodate a federation of existing directory services. In this respect, the X/Open Federated Naming Standard could be of use, together with protocols such as LDAP (Lightweight Directory Access Protocol). These standards allow for various existing proprietary and open directory schemes to coexist and to be used as a single, logical federated directory system.
The Open Group has formed partnerships with commercial and government agencies from several countries to provide solutions that will work in an international trading environment. The Open Group is also working with other organizations to integrate appropriate existing work, and recognises the need to incorporate the views of governments and other bodies that set governance policies in the commercial marketplace. The technology must be capable of supporting existing legal structures. Modifying laws is time-consuming and the existing structures have typically proved sufficient for moderating business so far.
The X/Open brand indicates that the vendor guarantees to the end-user customer that the branded product conforms to the standard, and will continue to conform, for the lifetime of the product. The use of the brand by is enforced by a legal contract between the vendor and The Open Group, and commits the vendor to correct any conformance deficiencies that may occur throughout the branded life of the product with a publicly available fix within a specified time.
The merger of X/Open and OSF has enabled The Open Group to provide a more complete range of security services and to offer technology to the marketplace that has been developed in a collaborative industry environment. The Distributed Computing Environment (DCE) is a prime example of such technology which offers a complete software environment for supporting secure distributed applications. Services supported by DCE include: Remote Procedure Call (RPC) for secure communications, the Directory Service, the Time Service which provides accurate time-stamping for distributed applications, the Threads Service which supports concurrency & parallelism in applications, and the Security Service.
The DCE Security Service supports a Secure RPC for the confidentiality and integrity protection of communications and distributed authentication services, both based on the Secure Communications Services and on Kerberos. Authorization tools are provided, and a single logical User Registry which eases the burden of managing user and group account information and policies.
DCE is already available from various suppliers, and development work is continuing to ensure that new capabilities are added and it continues to offer an attractive solution to ever-changing commercial environments.
The Open Group Research Institute has initiated a number of collaborative projects that aim to provide new secure capabilities and facilities for use in Intranets and on the Internet. Secure Enterprise Web for example, harnesses the security of DCE to make data and services available securely via the World-Wide Web. Secure Enterprise Web protects data from unauthorized access and modification, and enables the secure management of documents, servers, and users in a distributed environment, while seamlessly integrating with existing web components, (extends rather than replaces). Commercial products based on DCE Web, such as Dascom's IntraVerse WebStarter, are already available in the marketplace.
Further security-related advanced development projects are intended to extend robust security protection to the Java environment, and to enable JAVA applications to take advantage of Secure Enterprise Web security services such as: RPC, strong authentication, message encryption and integrity, robust access control and distributed naming services, as well as other secure applications built on top of DCE.
Security is an issue that has become central to the future business strategies of all enterprises. With the introduction of the X/Open Baseline Security 96 product standard, The Open Group has taken a major step in defining standards to address security within open systems computing environments.
Supported by vendors and customers, Baseline Security 96 resolves many of the problems brought about by the lack of standards among vendor products. As additional security products are introduced by The Open Group for distributed computing environments and the public network, organizations will be able to carry on truly global commerce more quickly, more easily and more cost-effectively.
Building on its success in delivering collaboratively developed technology such as DCE and Secure Enterprise Web to the marketplace, The Open Group continues to deliver real solutions that address current commercial requirements and environments.
Dedicated to the advancement of multi-vendor information systems, The Open Group is an international consortium of vendors, ISVs and end-user customers from industry, government, and academia. Under The Open Group umbrella, the Open Software Foundation, Inc. (OSF) and X/Open Company Ltd. (X/Open) work together to deliver technology innovations and wide-scale adoption of open systems specifications. The OSF hosts industry-wide, collaborative software research and development for the distributed computing environment. X/Open's brand mark is recognized worldwide as a guarantee of compliance to open systems specifications. The Open Group is headquartered in Cambridge, MA, with European headquarters in Reading, England and offices in Menlo Park, CA; Washington, D.C.; Brussels, Belgium; Grenoble, France and Tokyo, Japan.
###
© 1996 , The Open Group. All rights reserved.
Open Software Foundation, OSF, the OSF logo,
OSF/1, OSF/Motif and Motif are registered trademarks of the Open
Software Foundation, Inc. X/Open is a registered trademark and
the "X" device is a trademark of X/Open Company Ltd.
The Open Group is a trademark of the Open Software Foundation,
Inc. and X/Open Company Ltd. UNIX is a registered trademark in
the US and other countries, licensed exclusively through X/Open.
All other trademarks mentioned are the property of their
respective owners.
Permission is granted to reproduce any portion of the text or graphic images of this document provided that you prominently display both the copyright notice listed above and the following acknowledgment. Portions of this document have been reproduced with the permission of the copyright owner, The Open Group, Cambridge, MA.