The Open Group Cloud Ecosystem Reference Model – The Cloud Ecosystem Reference Model
The Cloud Ecosystem Reference Model serves as an abstract foundation for the instantiations of architectures and business solutions of an enterprise. It defines a flexible and agile collaborative enterprise Cloud Ecosystem. It also provides for an effective digital customer experience for sharing business information securely regardless of its underlying data location.
The Cloud Ecosystem Reference Model ensures consistency and applicability of Cloud Services within a wide variety of Enterprise Architecture management frameworks. Figure 1 describes the relationships and dependencies between the various enterprise frameworks to manage the life cycle of Cloud Services utilizing the Architecture Building Blocks (ABBs) identified in the Cloud Ecosystem Reference Model to deliver enterprise business solutions. Please refer to the TOGAF standard for further explanation of the concepts associated with Architecture Development Methods (ADMs) and management of frameworks.
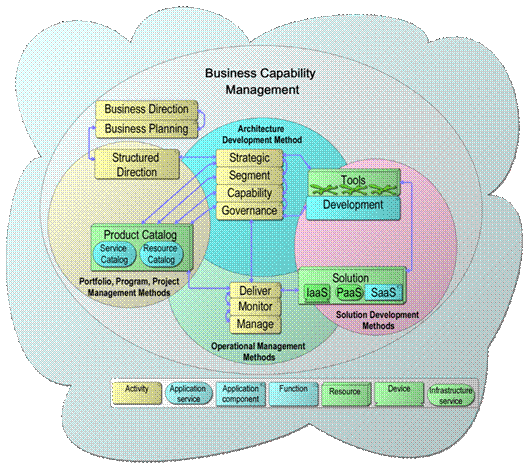
Managing Frameworks of an Enterprise Cloud Ecosystem
The Cloud Ecosystem Reference Model defines the major actors and their relationships and a minimum set of ABBs. The model describes the architectural capabilities to be realized and facilitated by at least one of the new or existing participants of an enterprise Cloud Ecosystem. The model establishes a common language for the various participants of an enterprise Cloud Ecosystem that supports the validations of Cloud Service Providers’ solutions to achieve architectural integrity of business solutions of an enterprise.
ABBs of the Reference Model are described in Chapter 2 and Section 3.1.
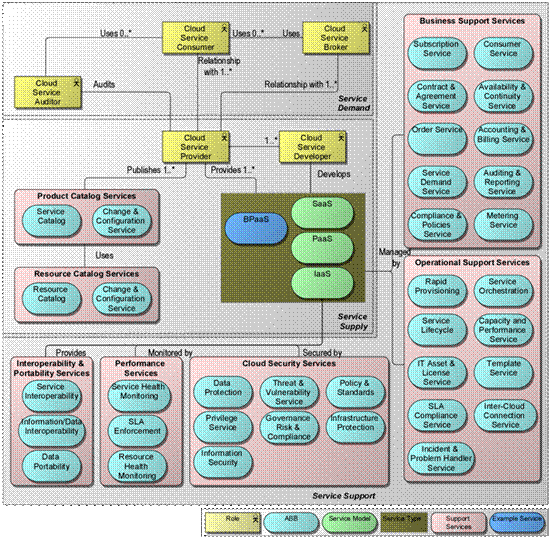
The Cloud Ecosystem Reference Model
The Cloud Ecosystem Reference Model should be considered as an extension of an Enterprise Architecture Model. The model can be used to define architecture for any specific scenario applicable for an enterprise utilizing Solution Building Blocks (SBBs) implemented by any new or existing participants of an enterprise Cloud Ecosystem. The visibility of these capabilities will vary according to the role(s) of the participants.
The Cloud Ecosystem Reference Model Taxonomy
This section describes the Cloud Ecosystem Reference Model Taxonomy to consistently apply a common business and IT taxonomy for interoperability.
Business Support Services
Business Support Services provide the business-related capabilities needed to simplify and support the end-to-end business activities of an enterprise Cloud Ecosystem. The following standard services will reduce complexity and simplify the enterprise business operations.
Business Support Services ABBs of the Cloud Ecosystem Reference Model
Architecture Building Blocks (ABBs) |
Description |
Accounting & Billing Service |
The Accounting & Billing Service generates and manages bills for the Cloud Service usage data using a set of predefined billing policies. Cloud Service Providers could allow production of one bill for multiple subscriptions of Cloud Services for the consumer and combining usage from multiple subscriptions to qualify for volume pricing discounts. It also manages other accounting-related activities (process payments, track invoices, etc.). |
Auditing & Reporting Service |
The Audit & Reporting Service provides a mechanism to record activities (including exceptions and events) and keeps them for an agreed time period to assist future investigations. Care must be taken to minimize the performance degradation and the risk of disruption to business processes. It generates reports to effectively perform client-facing business operations activities. |
Availability & Continuity Service |
The Availability & Continuity Service controls the redundancy, workload mobility between different Cloud Service Providers, and ensures that Cloud Services are built with high availability design practices and considerations. |
Compliance & Policies Service |
The Compliance & Policies Service defines, integrates, and aligns activities such as corporate governance and corporate compliance with applicable laws and regulations. It maintains an organizational structure, process, tools, and business policies to ensure adherence to applicable laws and regulations. |
Consumer Service |
The Consumer Service (aka Customer Management) provides an authoritative view to Cloud Service Consumers’ information to ensure effective care is provided and information about consumer relationships is well managed. |
Contract & Agreement Service |
The Contract & Agreement Service handles contract life cycle (set-up, negotiate, close, terminate, etc.) and the ways in which various aspects of Cloud Services are offered and managed for Cloud Service Consumers. The contract states the terms and conditions for service usage (constraints, costs, and billing information) by the Cloud Service Consumer and includes applicable Cloud Service policies, Service-Level Agreements (SLAs) – availability, performance, etc. – to ensure that Cloud Service Providers provision services that meet the defined agreement. |
Metering Service |
The Metering Service is essential for billing/charging Cloud Services and their underlying resource usages (i.e., Cloud Services and resources allocation and consumption). It provides a metering capability with some level of abstraction appropriate to the type of service (e.g., storage, processing, bandwidth, and active user accounts). |
Order Service |
The Order Service controls the life cycle of Cloud Service orders (from a Cloud Service provisioning request capture to de-provisioning). It utilizes Cloud Service configuration, service life cycle, service orchestration (if required), and accounting and billing services. |
Service Demand Service |
The Service Demand Service is to understand the business demand for Cloud Services (e.g., in the case of IaaS, demand in the form of bandwidth, memory, CPU capacity, support personnel, etc.) based on the past business activity patterns combined with the future business growth estimate. |
Subscription Service |
Cloud Service Providers could enable multiple subscription models for charging Cloud Services’ usage by utilizing the Subscription Service. These subscription models may include fixed, tier-based (e.g., Gold, Silver, and Platinum), pay-as-you-go payment terms (monthly, quarterly, annually). The Cloud Service Provider monitors allocation and consumption of Cloud Services and chargeback to its subscribed consumers based on subscription models. |
Operational Support Services
Operational Support Services enable the capabilities for efficient business operations of an enterprise Cloud Ecosystem.
Operational Support Services ABBs of the Cloud Ecosystem Reference Model
Architecture Building Blocks (ABBs) |
Description |
Capacity & Performance Service |
The Capacity & Performance Service (aka Workload Management) allows efficient allocation and optimal use of underlying Cloud Resources. It analyzes performance of running Cloud Services in real-time and automatically adjusts the workload. If applicable, it utilizes external Cloud Service Providers’ computing services by using inter-cloud connection services to meet the defined SLAs. |
Incident & Problem Handler Service |
The Incident & Problem Handler Service deals with any service-related incidents and associated problems and performs root cause analysis. It could store information in a knowledge support repository for further analysis that may include trend analysis to enable the evolution of the Cloud Services to prevent future incidents. |
Inter-Cloud Connection Service |
The Inter-Cloud Connection Service serves as a seamless connector from one cloud environment to another cloud environment (e.g., private cloud environment to external/public cloud environment) to enable Cloud Service interoperability. A Cloud Service connection ensures secure connectivity, traverses different network boundaries seamlessly, and enables performance improvement capabilities (e.g., compression). |
IT Asset & License Service |
The IT Asset & License Service controls licensing agreements of various aspects of Cloud Services that can be purchased and sold. Some Cloud Service Providers also allow Cloud Service Consumers to directly lease or buy licenses from the software/solution vendors or provide licenses on-demand. |
Rapid Provisioning |
Rapid Provisioning delivers architectural capabilities to quickly scale in or scale out computing resources normally delivered by at least one of the participating entities. Once self-subscribed to a catalog service, Rapid Provisioning capabilities automatically deploy Cloud Services based on a requested service capability. In a mature cloud environment, the Cloud Service Consumer could also have the capability to customize experience based on their role within the organization. |
Service Life Cycle |
Service Life Cycle (aka Service Delivery Management) controls the Cloud Services (including underlying Cloud Resources) life cycle from provisioning to de-provisioning dynamically (some Cloud Service Providers utilize workflow to manage the process). It also provides the visibility, control, and automation across cloud environments (e.g., private, public, and hybrid environments) to address business-critical challenges. |
Service Orchestration |
Service Orchestration serves as an efficient way to manage the Cloud Services (including underlying Cloud Resources) capacity and performance (it even instigates an external service gateway for workload management) automatically. It seamlessly coordinates Cloud Services in multiple cloud environments (e.g., internal/private and public cloud environments). |
SLA Compliance Service |
In order to ensure a high-level of service standards on Cloud Services, Cloud Service Consumers demand strict implementation of SLAs from Cloud Service Providers. Any degradation of service performance could have severe impact on revenue and end-user satisfaction. The SLA Compliance Service helps define SLAs and ensure their compliance and improve relationships with Cloud Service Providers. This service provides real-time assessment and SLA compliance reporting on Cloud Services. |
Template Service |
The Template Service provides re-creatable instances from service templates. In case of IaaS, the Template Service describes how the instances are to be configured (machine images, network connectivity, storage requirements, etc.) and deployed on a dynamic infrastructure environment. The Template Service also enables auto provisioning/re-deploying applications on a Cloud Service platform. |
Cloud Security Services
Cloud Security Services provide the broad set of service capabilities to protect data/information, software, and the associated infrastructure services of an enterprise Cloud Ecosystem. Refer to The Open Group White Paper: Security Principles for Cloud and SOA for principles that are widely applicable as guidance to secure systems in all environments.
Cloud Security Services ABBs of the Cloud Ecosystem Reference Model
Architecture Building Blocks (ABBs) |
Description |
Data Protection |
In the information age, data is an asset. However, most data remains valuable only if it is protected. Data Protection needs to cover all data life cycle stages, data types, and data states. Data stages include create, store, access, roam, share, and retire. Data types include unstructured data, such as word processing documents, structured data, such as data within databases, and semi-structured data, such as emails. Data states include Data At Rest (DAR), Data In Transit (DIT) (also known as “data in motion” or “data in flight”), and Data In Use (DIU). The controls of Data Protection are data life cycle management, data leakage prevention, intellectual property protection with digital rights management, and cryptographic services, such as key management and PKI/symmetric encryption. (See TCI – A Quick Guide to the Reference Architecture.) The Enterprise Data Management function described below consistently applies security policies to all data types, data life cycle stages, and states. |
|
Enterprise Data Management In a knowledge economy, information/data is a crucial enterprise asset that has to be managed in order to securely share information within an enterprise Cloud Ecosystem. The Enterprise Data Management functions have to execute for all of the life cycle phases for all classes of data. The key Enterprise Data Management functions (refer to The Open Group White Paper: An Information Architecture Vision) are data governance, information planning and architecture, information provisioning, records and archives provisioning, and information privacy. All manner of information/data has to be managed. Data can be classified as unstructured (human-processable only, such as an image); semi-structured which is machine-readable (e.g., an e-document), or structured which is machine-processable. Information is used by business users and consists of one or more classes of data (refer to The Open Group White Paper: An Information Architecture Vision). Metadata is data about the data (e.g., creator, date/time of creation, security classification, and so on) that has to be standardized and managed within an enterprise Cloud Ecosystem. Refer to The Open Group Guide: Cloud Computing Portability and Interoperability for detailed information. |
Governance Risk & Compliance |
Governance Risk & Compliance encompasses, integrates, and aligns activities such as corporate governance, enterprise risk management, and corporate compliance with applicable laws and regulations. Components include compliance management (which assures compliance with all internal information security policies and standards), vendor management (to ensure that service providers and outsourcers adhere to intended and contractual information security policies applying concepts of ownership and custody), audit management (to highlight areas for improvement), IT risk management (to ensure that risks of all types are identified, understood, communicated, and either accepted, remediated, transferred, or avoided), policy management (to maintain an organizational structure and process that supports the creation, implementation, exception handling, and management of policy that represent business requirements), and technical awareness and training (to increase the ability to select and implement effective technical security mechanisms, products, process, and tools). (This description is based on the definition in TC1 – A Quick Guide to the Reference Architecture. Refer also to The Open Group White Paper: An Architectural View of Security for Cloud.) |
Infrastructure Protection Services |
Infrastructure Protection Services secure server, end-point, network, and application layers. This discipline uses a traditional defense-in-depth approach to make sure containers and pipes of data are healthy. The controls of Infrastructure Protection Services are usually considered as preventive technical controls such as IDS/IPS, firewall, anti-malware, white/black listing, and more. They are relatively cost-effective in defending against the majority of traditional or non-advanced attacks. (This description is based on the definition in TC1 – A Quick Guide to the Reference Architecture. Refer also to The Open Group White Paper: An Architectural View of Security for Cloud.) |
Information Security |
The main objective of Information Security (aka Information Security Management) is to implement the appropriate measurements in order to minimize or eliminate the impact that security-related threats and vulnerabilities might have on an organization. Often Information Security will address privacy and confidentiality concerns; especially in international enterprises where national legislation may differ significantly and impact the transit and storage of data/information. Information Security is reliant on cloud-consistent security labeling (e.g., security classification) and compartmentalization as necessary. This is imperative if the cloud uses information rather than network-centric security. Other controls will dictate the security during data states including matters such as encryption protocols when data is in use, in transit, or at rest (DIU, DIT, DAR). (Refer to The Open Group White Paper: An Architectural View of Security for Cloud.) |
|
Risk Management Risk Management starts with the categorization and costing of information and related technology assets. Subsequently, risks are identified and classified along with the resultant management decisions to accept, mitigate, transfer, or avoid them. Risks are constantly monitored and reviewed whenever there are any changes to the cloud architecture. Dashboards for security management and risk management are used to measure and report the level of effectiveness of decisions and help the organization make new decisions that will maintain and improve that effectiveness. Analysis and plans for remediating residual risks are also part of the overall risk management framework. (Refer to TC1 – A Quick Guide to the Reference Architecture.) |
Policy & Standards |
Security policies are part of a logical abstraction of enterprise security architecture. They are derived from risk-based business requirements and exist at a number of different levels, including information security, physical security, business continuity, infrastructure security, application security, as well as the overarching business operational risk management. Security policies are statements that capture requirements specifying what type of security and how much should be applied to protect the business. Policies typically state what should be done, while avoiding reference to particular technical solutions. Security standards are an abstraction at the component level and are needed to ensure that the many different components can be integrated into systems. Internationally recognized standards for various aspects of security from standard bodies include ISO, IETF, IEEE, ISACA, OASIS, and TCG. Direction can also be provided in the form of operational security baselines, job aid guidelines, best practices, correlation of regulatory requirements, and role-based awareness. One way to approach security policy and its implementation is to classify information and associate policies with the resulting classes of data. (Refer to TC1 – A Quick Guide to the Reference Architecture.) |
Privilege Service |
The Privilege Service (aka Privilege Management) ensures that users have the access and privileges required to execute their duties and responsibilities with Identity and Access Management (IAM) functions such as identity management, authentication services, authorization services, and privilege usage management. This security discipline enables the right individuals to access the right resources across increasingly heterogeneous technology environments and meet increasingly rigorous compliance requirements. The technical controls of the Privilege Service focus on identity provisioning, passwords, multi-factor authentication, and policy management. This security practice is a crucial undertaking for any enterprise. It is also increasingly business-aligned, and it requires business skills, not just technical expertise. (This description is based on the definition in TC1 – A Quick Guide to the Reference Architecture. Refer also to The Open Group White Paper: An Architectural View of Security for Cloud.) |
Threat and Vulnerability Service |
This discipline (aka Threat and Vulnerability Management) deals with core security, such as vulnerability management, threat management, compliance testing, and penetration testing. Vulnerability management is a complex endeavor in which enterprises track their assets, monitor and scan for known vulnerabilities, and take action by patching the software, changing configurations, or deploying other controls in an attempt to reduce the attack surface at the resource layer. Threat modeling and security testing are also part of activities in order to identify the vulnerabilities effectively. (This description is based on the definition in TC1 – A Quick Guide to the Reference Architecture. Refer also to The Open Group White Paper: An Architectural View of Security for Cloud.) |
Performance Services
Performance Services are responsible for enforcing SLAs on Cloud Services, including measuring resource utilization, performance analysis in the cloud computing environment, and providing real-time assessment and reporting on resource/service performance.
Performance Services ABBs of the Cloud Ecosystem Reference Model
Architecture Building Blocks (ABBs) |
Description |
Resource Health Monitoring |
Resource Health Monitoring provides an integrated view of Cloud Resources health to achieve better performance, accountability, and business results to support cloud operational events and generate Cloud Resources performance reports. It also provides instrumentation capabilities to monitor defined SLAs. |
Service Health Monitoring |
Service Health Monitoring provides an integrated view of Cloud Services health to achieve better performance, accountability, and business results to support cloud operational events and generate Cloud Services performance reports. It also provides instrumentation capabilities to monitor defined SLAs. |
SLA Enforcement |
SLA Enforcement ensures that SLAs defined in the service contract are rigidly enforced in order to avoid any applicable penalties. Captured data related to SLAs also provide opportunities to make adjustments to contracts and agreements during the subscription renewal process. |
Interoperability and Portability Services
Interoperability and Portability Services provide Cloud Services to achieve effective integration with all the participants of an enterprise Cloud Ecosystem.
Interoperability and Portability Services ABBs of the Cloud Ecosystem Reference Model
Architecture Building Blocks (ABBs) |
Description |
Information/Data Interoperability |
Information/Data Interoperability provides the Cloud Service Consumer with the ability to effectively manage the life cycle of both structured and unstructured data of an enterprise. It provides mechanisms to classify data, access policies, and information protection to adhere to compliance regulations and legislation. Information/data interoperability requires a consistent structure for behavior data interoperability (i.e., rules and data behavior). Semantically consistent information allows data to be shared and re-used across applications and enterprises boundaries. This could include the use of cloud-specific metadata-based semantic standards such as The Open Group Universal Data Element Framework (UDEF) (refer to The Open Group UDEF webinar) or the US Government National Information Exchange Model (NIEM). This would enable the information/data to be shared and re-used within an enterprise Cloud Ecosystem. Refer to The Open Group Guide: Cloud Computing Portability and Interoperability for detailed information. |
Service Interoperability |
Service Interoperability is the ability of Cloud Service Consumers to use their data and services across multiple Cloud Service Providers with a unified management interface (refer to NIST SP 500-292). The following highlights interoperability/portability as service model levels. Refer to The Open Group Guide: Cloud Computing Portability and Interoperability for detailed information. |
|
IaaS Interoperability IaaS Interoperability (aka System Portability – refer to NIST SP 500-292) provides a mechanism for Cloud Service Providers to provision a workload (e.g., compute) either an internal environment or onto an external Cloud Provider’s environment and seamless migration of information about the service and its underlying resources. |
|
PaaS Interoperability The PaaS level of interoperability focuses on the ability to provide seamless coordination in the development and deployment of platform services and associated licenses. Currently there is little or no portability provided at the PaaS level. |
|
SaaS Interoperability Cloud Service Consumers expect to have the ability to support critical SaaS applications’ features on a variety of channels (e.g., web, mobile, smart phone, etc.). Interoperability on common features is usually supported (where possible) by utilizing presentation abstraction. |
Data Portability |
Data Migration Data Migration provides an automated mechanism to transfer data from one cloud environment to another or to other computing systems. |
|
Data Synchronization Data Synchronization is the mechanism to ensure consistency across the Cloud Ecosystem to a single set of source data for all duplicated target data storage and vice versa. It ensures the continuous coherency of the data over time. It is a fundamental requirement for globally distributed applications (e.g., file synchronization between regions, and base information synchronization between catalogs). For example, a common service catalog data model that allows data synchronization capabilities between a Cloud Service Provider’s service catalog and a Cloud Service Consumer’s product catalog. |
Product Catalog Services
The product catalog of the Cloud Ecosystem provides catalog information (description, type, associated base SLAs, etc.) about an enterprise’s Cloud Services.
Product Catalog Services ABBs of the Cloud Ecosystem Reference Model
Architecture Building Blocks (ABBs) |
Description |
Change & Configuration Services |
The Change & Configuration Services ensure that the configuration of Cloud Services remains compliant with the changes in policies and compliance. It maintains an accurate configuration of Cloud Services offered in the catalog. It also ensures that the Configuration Management Database (CMDB) information is highly available, secured, and in compliance with applicable licensing terms and conditions. |
Service Catalog |
The Service Catalog provides flexible and easily configurable catalog information (description, type, associated base SLAs, etc.) and enables a mechanism for Cloud Service Consumers to subscribe to listed services. The information is generally collected through a self-service Cloud Service provisioning portal and allows cloud consumers to describe and manage Cloud Services easily. The service catalog includes information about the Cloud Service (pricing, payment terms and conditions, etc.), could support multiple pricing models (pay-as-you-go, tiered models, etc.), and includes technical, business, and compliance constraints. The cloud service catalog integrates with the CMDB to define and manage information about instances of catalog services and their relationship with physical and virtual infrastructure resources. The service catalog seamlessly integrates with the cloud security service and Cloud Services management tools (business and operational management tools). The service catalog could also describe the Cloud Service Provider’s ability to meet a cloud performance rating (a common way to evaluate and determine competitive advantage). |
Resource Catalog Services
The Resource Catalog Services manages the underlying Cloud Services resources of an enterprise Cloud Ecosystem.
Resource Catalog Services ABBs of the Cloud Ecosystem Reference Model
Architecture Building Blocks (ABBs) |
Description |
Change & Configuration Service |
The Change & Configuration Service for resources ensures that the configuration of Cloud Services remains compliant with the changes in policies and compliance. It maintains an accurate configuration of the Cloud Services offered in the catalog. It also ensures that CMDB information is highly available, secured, and in compliance with applicable licensing terms and conditions. |
Resource Catalog |
The resource catalog manages information about the resources required to support Cloud Services provisioning requests captured through the self-service Cloud Service management provisioning channel. The resource catalog also includes technical, business, and compliance constraints. |
Enterprise Architecture Principles of the Cloud Ecosystem
Enterprise Architecture Principles of the Cloud Ecosystem define the underlying rules and guidelines for the use of the ABBs identified in the Cloud Ecosystem Reference Model to manage the life cycle of Cloud Services across the enterprise. These principles should be in alignment with other enterprise principles and reflect an architectural consensus across the enterprise. The principles ensure consistency and integrity of the Enterprise Architecture and form the basis for making future decisions pertinent to an enterprise’s Cloud Ecosystem.
Principle Name |
Auto-provisioned sharable system infrastructure. |
Description |
The underlying computing resources of IaaS (e.g., storage, compute, and network) are shared and auto-provisioned to support an efficient system infrastructure. |
Rationale |
In order to meet business objectives to maximize profit, the IaaS Cloud Service Provider’s underlying computing resources serve using a multi-tenant environment. IaaS can seamlessly move workloads around to lower overhead and meet defined SLAs. |
Implications |
IaaS should have a built-in capability of automated provisioning and dynamically move workload to meet defined SLAs. Business and service performance impact due to shared IaaS infrastructure should be well understood to avoid any undesired outcome. Cloud Service Providers should enable mechanisms to protect one tenant from other tenants. Auto-provisioning must prepare for peaks in load (e.g., higher volume of order and usage of computing resources due to advertised sale) with the use of cloud bursting. Cloud bursting is a way to address peak load by augmenting computing resources with an external IaaS provider’s computing environment. |
Principle Name |
Cloud solutions are designed to address performance variance. |
Description |
Cloud solutions that use common and public networks, using the Internet Protocol (IP), should expect unreliable service due to performance variance, variable latency, and network failure. |
Rationale |
One of the essential characteristics of cloud computing is to have cloud capabilities accessed through the standard and public Internet. Cloud solutions should be designed to address unreliable IP service and variance in latency. |
Implications |
Cloud solutions should be designed to seamlessly handle network failure and address how to meet performance-related SLAs. Data should be well protected in all stages of data (DIU, DAR, and DIT). Built-in capabilities need to be provided to deal with communications latency variance. |
Principle Name |
Automated ways to measure and optimize cloud solutions. |
Description |
Cloud Services solutions should enable automated ways to measure allocation and consumption of Cloud Services and optimize the service usage by leveraging metering capability. |
Rationale |
In order to minimize investment on Cloud Services, Cloud Services solutions should provide real-time transparency on Cloud Services utilization to both Cloud Service Provider and Cloud Service Consumer. |
Implications |
Cloud Services solutions should be designed with built-in mechanisms to capture resources allocation, consumption, and produce measurements data. Provide real-time (or near real-time) assessment reports to efficiently respond to demand/usage of Cloud Services solutions. Although profiling resource usage by any cloud solution in a multi-tenant cloud environment will be challenging, it would be required to optimize the usage to ensure accurate metering. Evaluate measurements data and make any changes to optimize Cloud Services solutions. |
Principle Name |
Automatic provisioning to enable horizontal scaling for distributed workload. |
Description |
Cloud Service Providers seek horizontal scaling (simultaneous process of data across multiple machines) to take advantage of larger virtual machine capabilities that could be rapidly and automatically provisioned to meet the requirements of parallel processing. |
Rationale |
Where possible, Cloud Service Providers are looking to utilize their larger virtual machines. Comparatively, horizontal scaling allows Cloud Service Consumers to process large amounts of data efficiently with minimum investment (e.g., the use of Hadoop and MapReduce types of applications). |
Implications |
Cloud solutions will have to be designed specifically for loosely-coupled distributed computing with fine-grained processing which could also promote easier workload movement. Larger data sources might require partitioning into smaller sets of data sources. |
Principle Name |
Loosely-coupled Cloud Services. |
Description |
Ensure that SaaS, PaaS, and IaaS are loosely-coupled. For example, a Cloud Service Consumer of PaaS does not control the underlying cloud infrastructure resources (e.g., compute, storage, and network). |
Rationale |
Cloud Services are designed to support dynamic and scalable cloud environments. |
Implications |
Minimize customization of Cloud Services to effectively support a multi-tenant deployment model. Well-defined separation of concerns in a cloud environment. Figure 3 illustrates the scope of control between Cloud Service Provider and Cloud Service Consumer. For more details, refer to Section 2.7 of NIST SP 500-292. |
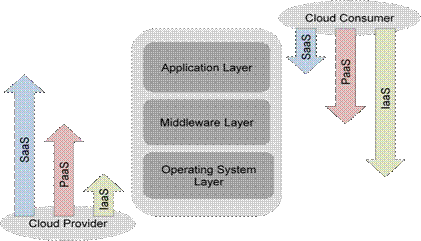
Scope of Control between Provider and Consumer (NIST SP 500-292)
Principle Name |
Cloud Service abstraction and control. |
Description |
Ensure that Cloud Services are securely exposed with the appropriate level of abstraction and hide implementation details of a Cloud Service. |
Rationale |
Cloud Service abstraction provides the right separation and hides the implementation details to ensure service agility. |
Implications |
Ensure there is a level of abstraction that separates the concept/interface and implementation details of Cloud Services. Ensure that all essential characteristics of Cloud Services (e.g., resource pooling, broad network access, measured service, rapid provisioning, etc.) are maintained without exposing implementation details. For example, in the case of IaaS, resource abstraction components include software elements, such as hypervisors, virtual machines, virtual data storage, and other computing resource abstractions. Ensure there are appropriate controls in place to provide secure and reliable usage of underlying service resources. |
Principle Name |
Multi-tenancy. |
Description |
A cloud computing model must support tenant and solution isolation among multiple tenants of the cloud. |
Rationale |
Cloud computing stores clients’ assets (information and operational processes applications) in servers distributed “who knows where”, so it is critical that each client’s assets are kept securely separated from the assets of other clients, irrespective of the storage media and processing resources that each client may also use in the cloud. |
Implications |
Cloud Service Providers offer assurances that they provide secure isolation between the assets of each of their clients. While this is difficult for them to evidence, their isolation control mechanisms seem to demonstrate success over this capability. SLAs may be required that guarantee separation of concerns with appropriate penalties. |